The target computer or domain controller challenge and check the password and store password hashes for continued use. Installing using Kerberos.
The code will print Authentication Scheme.

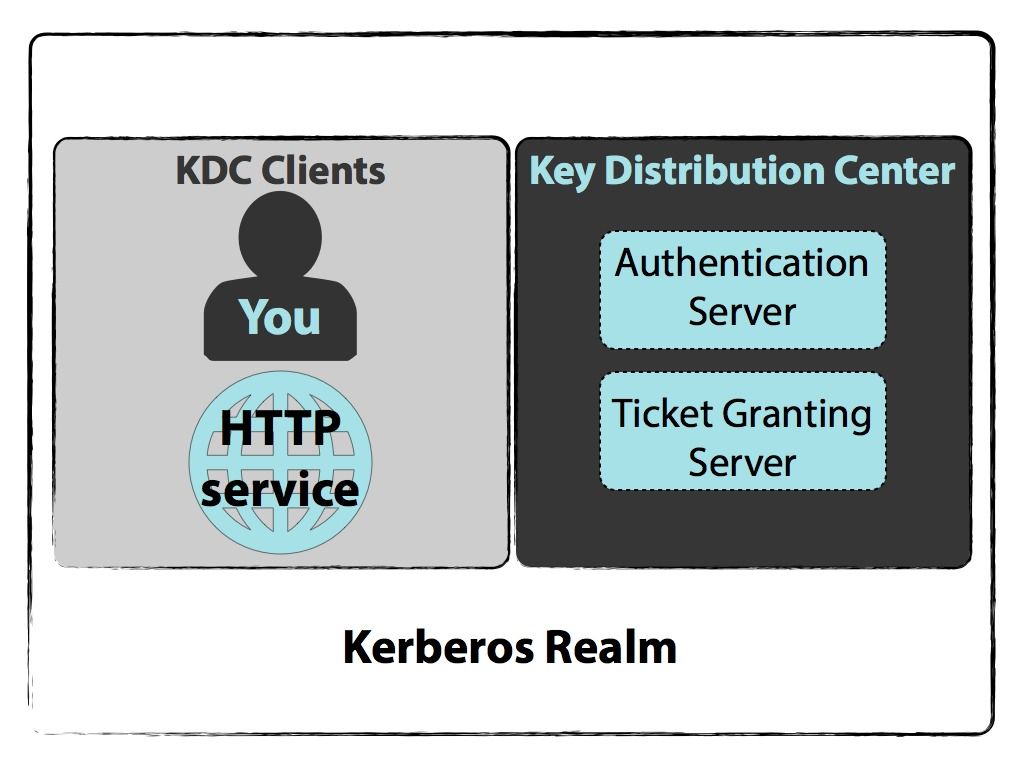
Kerberos authentication. Kerberos ˈ k ɜːr b ər ɒ s is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. After initial domain sign on through Winlogon Kerberos. The protocol was named after the character Kerberos or Cerberus from Greek mythology the ferocious three-headed guard dog of Hades.
Briefly when a client needs to request a service it does five steps as shown in the following diagram. Applying the Kerberos authentication on the client application. Generates a new key for the.
Run the following code on a Windows machine with working Kerberos authentication to verify if the aforementioned is true. It could be a problem to rewrite the code for some applications in order to make them Kerberos aware. This guide assumes a working Kerberos setup already exists.
Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services. The biggest difference between the two systems is the third-party verification and stronger encryption. Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials.
KERBEROS to the console if successful. NTLM stands for NT Lan Manager and is a challenge-response authentication protocol. Introduction My team recently configured Kerberos Authentication in SharePoint 2013 web applicationWe have captured step by step process of how to configure Kerberos Authentication in SharePoint 2013.
Kerberos can only be adopted by Kerberos aware applications. Using Kerberos authentication from Unix Machines on the same domain. No additional run-time flags.
I want to explain more about steps 2 and 4. This article will help the SharePoint administrators who want to configure the Kerberos Authentication in their SharePoint web applications. Before Kerberos Microsoft used an authentication technology called NTLM.
Describes a very simple demo based on part I. In step 2 the KDC does the following. When using Kerberos authentication in Remedy Single Sign On you need to remember to enable Kerberos authentication for the browsers youre using.
Overview of the Kerberos authentication process.

Authentication Fails When A Windows Client Accesses A Cifs Share Because The Kerberos Authentication Ticket Is Cache In 2021 Windows Client Fails Microsoft Corporation

Apache Tomcat Kerberos Authentication Tutorial Examples Java Code Geeks 2016 Coding Tutorial Apache

Pin On News Office 365 Azure And Sharepoint

Kerberos Architecture Computer Help Windows Server Microsoft

Kerberos Authentication Architecture Ile Ilgili Gorsel Sonucu Cryptography Architecture Kas
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Vulnerability

Troubleshooting Kerberos Authentication In Sharepoint Www Dfsmrecruitment Com Sharepoint Event Id Custom Home Bars

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Mongodb Authentication With Kerberos Regular Expression Data Storage Reading

Domain Controller Certificate Template Kerberos With Regard To Quality Domain Co In 2021 Certificate Template Certificate Templates Certificate Of Achievement Template

Authentication Fails When A Windows Client Accesses A Cifs Share Because The Kerberos Authentication Ticket Is Cached In 2021 Windows Client Fails Clients

Apache Flink Provides First Class Support For Authentication Of Kerberos Only While Providing Effortless Requirements To All C Apache Security Activity Monitor






